Updating the Intel Windows 10 processor microcode. Intel has released a microcode update for several CPU generations
Hello dear friends, with you Artyom.
In January of this year, there were reports of new hardware vulnerabilities in Intel and AMD processors.
Not so long ago, the microcode updates for Intel processors (revision 84) came, and I decided to check how things are in practice.
Although the information is already known to everyone, I will still tell a short history.
Hardware vulnerabilities of processors received the names of Meltdown and Spectre, and they revealed their researchers from the Google Project Zero group.
Spectre has two attack options CVE-2017-5753 and CVE-2017-5715 code names.
Meltdown has one attack option under the CVE-2017-5754 code name.
P.. S.. CVE is a reduction from English " COMMON. Vulnerabilities. and. Exposures."- Database of well-known information security vulnerabilities.
Seeing these designations to the descriptions of the patch, you will immediately understand what for which and for what.
Moreover, it is Meltdown to operate in practice that all modern Intel processors are exposed to.
In order to get rid of Meltdown, you need to update the processor microcode or to disappear the kernel of the operating system.
Spectre is more difficult to embody into reality, however, to eliminate vulnerabilities, it is necessary to drain each program you used.
AMD chips are less susceptible to the MeltDown type vulnerabilities (although it was originally stated that not at all).
The malicious code of this type works on them extremely slowly, but still works.
Spectre type vulnerabilities are subject to processors and AMD, and Intel, here without options.
Processors with ARM architecture are also subject to the same vulnerabilities, but now it will be discussed only about computers with the processors of the X86-64 family.
P.. S.. Security studies never stop and can always appear, including AMD and Intel processors.

Important remark! While the video was in the installation and wrote a clock material to the site, new research on the security of processors appeared.
New options for implementing the Spectre vulnerabilities, which received code names CVE-2018-3640 (the so-called version of the attack 3a) and CVE-2018-3639 (An option 4) are revealed.
Let me remind you that Specter is fixed by updating the software used, such as browsers and so on.
However, from the last version of the CVE-2018-3639 attack, you will also need to update the processor microcode on Intel chips, which may be somewhat reduced performance.
AMD claims that the company's chips will not need a new microcode from the specified attacks, and everything will cost the usual patch of Windows and other software.
These vulnerabilities have a low hazard priority for ordinary home computers.
Since there are no new updates yet, I focus on the original topic of your video.
It will be about the microcode of Intel processors, but the microcode is still different and does not correct the option of the SPECTRE 4 attack.
If you use the Windows family operating systems, these links will be useful for you:
Here you can find all current patches (and their names), which correct the vulnerability of this group.
For example, the first patch for Windows 10 came out on January 3, 2018 under the name KB4056892.
However, there was a problem in the fact that Meltdown software corrections reduced the performance of the Intel processors.
I somehow still have no free time to spend your small tests.
However, now with the release of new versions of firmware for motherboards, I am wondering how things are in this area.
I use the Motherboard ASRock Z370 Gaming K6 and accordingly appeal to the official site of the manufacturer, for downloading fresh BIOS.
The updated microcode for Intel processors appeared in the BIOS version 1.60, which came out on March 2, 2018.
I will put even a more recent version of the BIOS version 1.80, which I saw the light on March 26, 2018.

To begin with, it is interesting for me to test the corrections for the microcode of the processor, without additional software floors.
The operating system uses Windows 10 version 16299.371 without additional patches from Meltdown and Spectre hardware vulnerabilities.
P.. S.. All conclusions made will concern only new Intel processors, because for old motherboards, new BIOS versions are unlikely to appear.
If it is interesting for you, you can make tests with software plexus and on older Intel processors.
Full configuration of my computer:
CPU: Intel Core i5 8600K.
Cooler processor: ARCTIC COOLING LIQUID FREEZER 240.
Maternal pay: ASRock Fatal1ty Z370 Gaming K6.
Operative memory: GOODRAM IRIDIUM DDR4 2400 MHz (2 × 8 GB IR-2400D464L15S / 8G).
Video card: ASUS DUAL GTX 1060 6 GB (Dual-GTX1060-O6G).
Drives: SATA-3 SSD PLEXTOR M5S and SATA-3 HDD Seagate 1 TB (ST1000DM003).
Housing: Fractal Design Define R5.
Block nutrition: Fractal Design Edison M 750 Watt.
The first test is the performance of casheres of the central processor and RAM inAida. 64 Cache. & Memory. Benchmark..

As you see, some significant differences in the operation of the RAM subsystem and the processor caues do not.
The next test affects the work of the disk subsystem.
Unfortunately, I do not have a speed M.2 SSD drive, so I will test my Plextor M5S on the usual SATA-3.
As a result, almost identical results are obtained in the ATTO Disk Benchmark test.

The same applies to the indicators in CrystalDiskMark 5.2.1 test.

Performance test in CrystalDiskMark and the new Intel processor microcode. Spectre and Meltdown.
At least for SATA-3, the performance drop in read and record operations is not observed.
The following test 7zip, which will show performance when packing and unpacking archives.

There is still a picture, the difference in performance when installing a new fixed BIOS is not any.
Since I create content, I could not leave the editing of the video rollers aside.
As a mounting program, I use Vegas Pro 13 and regardless of the BIOS version used, the rendering time has not changed.

Video sources have 1080p resolution, bitrate 50 megabit / c and with a frequency of 50 frames per second.
As a profile for the render, Sony AVC / MVC was selected with a bit rate of 16 megabits / c, all other profile settings you see on your screens.

Now let's talk about games a little.
Those projects that have been installed on the computer at the moment (Assassin's Creed Origins, Farcry 4 and Crysis 3) took part in the tests.
All frame rates were removed using the MSI Afterburner 4.4.2.
In general, the results do not need commenting.

Performance tests in Assassin's Creed Origins games. Spectre and Meltdown.


If you use the new version of the processor microcode for revisions 84, then it is impossible to notice the difference in performance - everything works quickly and quickly.
It would be the only way to look at the work of M.2 SSD drives with the NVME interface.
Perhaps in the future I will spend another series of tests with software piping for Windows 10 and with the simultaneously installed fixed microcode of the central processor.
I hope you were interested. If so, then share my note on social networks with your friends.
So there will be much more such notes :)
Also, do not forget to join the VKontakte group and subscribe to YouTube Channel.
Acquired on Aliexpress in the Intel DG965SS motherboard (with LGA775 connector). You can, of course, to remake the LGA771 in the LGA775 itself, but at a price of $ 6.5 dollars for the processor it is much easier to take it and the Chinese.
When using Intel Xeon 5320, the Windows 10 operating system earned only when the "Core Multiplexing" mode is turned off in the bios (unlike perfectly working Ubuntu 17.10). In this case, the processor worked only in single-threaded mode, so, according to the CPU-Z test, the performance in multi-threaded mode was 2 times lower than that of Intel Core 2 Duo E6300, to replace which Xeon was bought.
It turned out that the microcodes of the processor should be updated. You can do this in the program mode, and in Ubuntu, the head is easier than in Windows 10. Yes, and in the latter you need to take care that the microcodes are updated with each download. It is also possible to update microcodes and bios, at least some BIOS from Award, Ami, Phoenix, especially in versions before UEFI.
Intel motherboards are much smaller. And not surprising. Intel DG965SS had to be very good to tinker.
Before updating microcodes, you need to install the processor, the support of which we want to provide. If you need to install another processor, then the procedure will have to repeat.
Some instructions suggest creating a boot diskette, because Not all computers allow you to load in the flash drive. I made a bootable USB flash drive with Freedos using a free RUFUS open source application (for this you need to mark the "Create a Bootable Disk Using" checkbox and select the "Freedos" item from the list).
You can optimize the work of Intel or AMD installed in your computer, setting the latest version of its microcode. Optimization is achieved mainly due to the correction of the error of the standard microcode derived from the firmware of the motherboard.
The BIOS / UEFI firmware updates of your motherboard usually contain new versions of microcodes for the main processor supported by the motherboard. For this reason, first of all, you should make sure that the newest version of BIOS / UEFI is used.
This manual allows you to optimize the work of only those central processors that were developed by Intel and AMD.
Notes:
- Installing software package with microcodes can lead to unstable computer operation. For this reason, this package should be installed only when there are any problems associated with the functioning of the central processor of your computer!
- Do not install the software package with the microcodes of central processors if it is released earlier than the BIOS / UEFI Motherboard Firmware of your computer!
1. Central Processors manufactured by Intel
In the case of the use of the central processor manufactured by Intel, you can act described below.
Note: Do you need a software package with microcodes of central processors manufactured by Intel, newer than what is in the official repository of the distribution? In this case, you can download the software package file with expansion. .deb. of
Synaptic package manager Software.
Synaptic package manager"Search on a computer"), enter a request "Synaptic" "Synaptic Package Manager" Synaptic package manager "Search" "Microcode" And click the button "Search" Next to him.
3.201501106.1 (In this case, version 3 of the package was created on November 6, 2015).
« intel-Microcode » And click the button "Apply"
dmesg | Grep Microcode.
ENTER
2. Central Processors manufactured by AMD
In the case of the use of AMD manufacturing processors, this manual will be relevant only for those that have been released after 2006 (AMD K10 and newer). If one of these central processors is installed in your computer, you can act described below.
Note: Do you need a software package with microcodes of central processors manufactured by AMD, newer than what is in the official repository of the distribution? In this case, you can download the software package file with expansion. .deb. From the repository of the Debian distribution, which places the packets of the newest versions. After downloading the package file, you should find it using the file manager and use a double click to install microcodes into the system. At the end of the installation, you must restart the computer.
A. If you use the Ubuntu distribution, you will have to install Synaptic package manager (This can be done using the application Software.). In Linux Mint, this package manager is present immediately after installation.
B. First of all, run Synaptic package manager. In the Ubuntu distribution for this purpose, click on the White Ubuntu logo at the top of the side panel ( "Search on a computer"), enter a request "Synaptic" and choose the first of the proposed application options. "Synaptic Package Manager". You do not need to use the Fast Software Package Software Package Field Synaptic package managersince the corresponding mechanism is unreliable; Instead, press the button "Search" On the toolbar, in the search field that opens the dialog box, enter a request "AMD64-MICROCODE" And click the button "Search" Next to him.
C. Now you should check the date of creation of a software package with microcodes of central processors: This package must be created later than the BIOS / UEFI firmware of your computer's motherboard! The creation date of the package under consideration is reflected in its version number, for example 2.20160316.1 (In this case, version 2 of the package was created on March 2, 2016).
D. It's time to check the box opposite the name of the software package. "AMD64-MICROCODE" And click the button "Apply" On the application toolbar.
E. After completing the software package, you need to restart the computer.
F. After a reboot it is necessary to check the correctness of the loading of one of the installed microcodes by entering the following command in the terminal window (use the copy / insert functions in order to avoid errors):
dmesg | Grep Microcode.
After entering the command, press the key ENTER For its execution. If the microcode was successfully loaded, you will see several messages about it.
Want to know about other settings and work techniques with Linux systems? This website contains a large number of similar materials.
Actually, the original method, snap and microcodes can be found (directly by AMI instructions), and in most cases the use of this method does not bear any problems and does not have underwater stones, but I regularly encountered such a problem with my practice:
Those. There was a banal lack of free space inside the image. When you modify the BIOS for yourself for a specific processor, you can not pay attention to this, because You can always upload only one microcode to your processor, or remove some old microcode to release the place, but when you modify the stream, you need to search for another solution, compromise.
As a compromise, I chose the following solution - we take the latest modes of microcodes for all Core generation processors in all designs (Celeron E, Pentium E, Core 2 Duo, Core 2 Quad, Xeon * 3xxx / * 5xxx) and replacing them all that was before . The set of microcodes turned out the following:
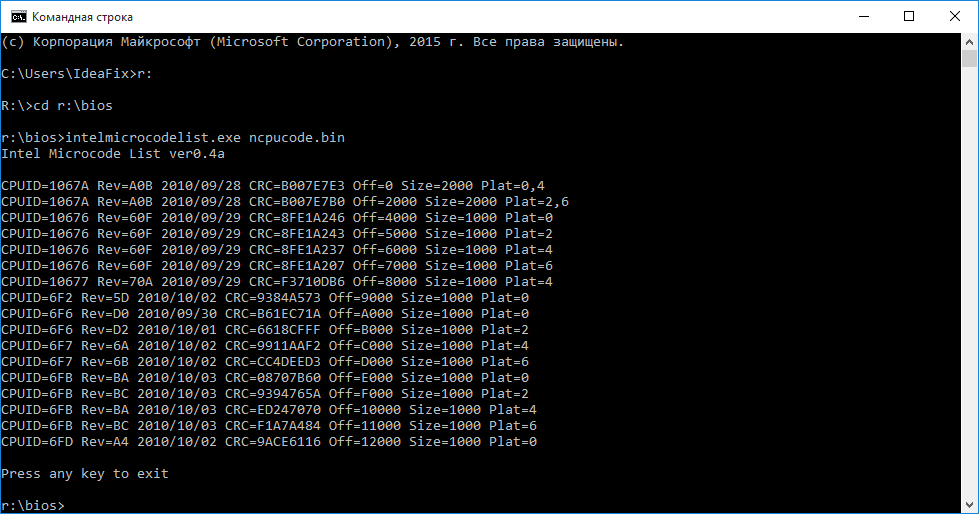
The volume of this set is only 76 kilobytes. This file turned out by combining these files:
cPU00010676_PLAT00000001_VER0000060F_DATE20100929.BIN.
CPU00010676_PLAT00000004_VER0000060F_DATE20100929.BIN.
CPU00010676_PLAT000010_VER0000060F_DATE20100929.BIN.
CPU00010676_PLAT00000040_VER0000060F_DATE20100929.BIN.
CPU00010677_PLAT00000010_VER0000070A_DATE20100929.BIN.
CPU0001067A_PLAT00000011_VER00000A0B_DATE20100928.BIN.
CPU0001067A_PLAT00000044_VER00000A0B_DATE20100928.BIN.
CPU000006F2_PLAT00000001_VER0000005D_DATE20101002.BIN.
CPU000006F6_PLAT00000001_VER000000D0_DATE20100930.BIN.
CPU000006F6_PLAT00000004_VER000000D2_DATE20101001.BIN.
CPU000006F7_PLAT00000010_VER0000006A_DATE20101002.BIN.
CPU000006F7_PLAT00000040_VER0000006B_DATE20101002.BIN.
CPU000006FB_PLAT00000001_VER000000BA_DATE20101003.BIN.
CPU000006FB_PLAT00000004_VER000000BC_DATE20101003.BIN.
CPU000006FB_PLAT00000010_VER000000BA_DATE20101003.BIN.
CPU000006FB_PLAT00000040_VER000000BC_DATE20101003.BIN.
CPU000006FD_PLAT00000001_VER000000A4_DATE20101002.BIN.
The modification procedure itself has also changed a bit and became not easier, then faster:
Step 1 - Open the BIOS image in the MMTOOL program: 

Step 2. - To check, go to the last tab (CPU Patch) and see the number of microcodes. Here are them for example 31 pieces: 
Step 3. - Go to the Replace tab and look for "P6 Micro Code" on it: 
Step 4. - By selecting "P6 Micro Code", click the button of the Ikshchi, select the ncpucode.bin file, described above and replacing it with the Replace button: 


Step 5. - To check, go to the last tab (CPU Patch) and see the number of microcodes. After the microcodes change, 17 remains, the latest version: 
The fundamental difference with the order of modification described on delidded.com is not. In most cases, it is not the same at the output, but the processor receives the desired microcode. From subjective positive moments, I would like to pay attention to only the fact that microcodes are guaranteed to update all current processors, whether "civil" or "server", as well as practically no risk of getting a message about the lack of space. Although, in my practice, there was not enough space for such a set of microcodes a couple of times, it was with BIOS for ECS P4M900T-M and ECS P4M900T-M2 boards, which are generally compatible with Xeon E5450.
By tradition, a public link to the archive with tools - (Zip, 234Kb). Archive contains executable file Mmtol.exe. (version 3.22 BKMOD), File with microcodes for all 45 / 65nm Core / Xeon generation processors ncpucode.bin., as well as two files 45nm.bin. and 65nm.bin. With microcodes only on 45NM processors and only 65nm. Using these files can be useful in cases when it is necessary to release an additional volume in the BIOS, for example, for a new Firmware which is a controller, network, disk, etc.
! Nb.: Nor in the ncpucode.bin file, nor in the files 45nm.bin / 65nm.bin there is no support for Pentium 4 processors, Celeron (without alphabetic indexes), Pentium D, Celeron D and Xeon W (Xeon 5080 for example). These are Netbrust generation processors.
 Windows Installer package error when installing iTunes and its elimination
Windows Installer package error when installing iTunes and its elimination View basic information about your Windows Computer
View basic information about your Windows Computer Erase the app from the smartphone
Erase the app from the smartphone