What is man in the middle. Detection of a man-in-the-middle attack (Man in the middle, MitM attacks)
Denoting a situation when an attacker is able to read and modify at will messages exchanged by correspondents, and none of the latter can guess about his presence in the channel.
Wikimedia Foundation. 2010 .
See what "Man in the middle (attack)" is in other dictionaries:
Man in the middle attack, MITM attack (English Man in the middle) is a term in cryptography that refers to a situation where a cryptanalyst (attacker) is able to read and modify messages exchanged at will ... ... Wikipedia
- ... Wikipedia
Cryptanalysis (from the Greek κρυπτός hidden and analysis) is the science of methods for obtaining the initial value of encrypted information without having access to the secret information (key) necessary for this. In most cases, this means ... ... Wikipedia
A hacker attack in the narrow sense of the word is currently understood by the phrase "Assault on a security system", and tends to be more like the meaning of the following term Cracker attack. This happened due to a distortion of the meaning of the word "hacker" ... Wikipedia
- (from other Greek κρυπτός hidden and analysis) the science of methods for decrypting encrypted information without a key intended for such decryption. The term was introduced by the American cryptographer William F. Friedman in 1920. Informally ... ... Wikipedia
In which an attacker, having connected to a channel between counterparties, intervenes in the transmission protocol, deleting or distorting information.
Encyclopedic YouTube
1 / 3
✪ #4 HOW TO BECOME A HACKER? "Attack of the Middleman"! |HACKING from A to Z|
✪ MiTM attack on iOS. Technique and aftermath
✪ Bitcoin Chronology of Hacker Attacks and Exchange Hacks in the Cryptocurrency Market (2012 - 2018)
Subtitles
Principle of attack
The attack usually begins with listening to the communication channel and ends with the cryptanalyst trying to replace the intercepted message, extract useful information from it, and redirect it to some external resource.
Suppose object A plans to send some information to object B. Object C has knowledge about the structure and properties of the data transfer method used, as well as the fact that the planned transfer of the actual information that C plans to intercept. To carry out an attack, C “presents itself” to object A as B, and to object B as A. Object A, mistakenly believing that it is sending information to B, sends it to object C. Object C, having received the information and performing some actions with it (for example, , copying or modifying for their own purposes) sends the data to the recipient itself - B; object B, in turn, believes that the information was received by him directly from A.
Attack example
Injection of malicious code
A man-in-the-middle attack allows a cryptanalyst to inject his code into emails, SQL statements, and web pages (i.e., allows SQL injection, HTML/script injection, or XSS attacks), and even modify user-loaded binaries to to access a user account or change the behavior of a program downloaded by the user from the Internet.
Downgrade attack
The term "Downgrade Attack" refers to such an attack in which the cryptanalyst forces the user to use less secure functions, protocols that are still supported for compatibility reasons. This type of attack can be carried out on the SSH , IPsec and PPTP protocols.
To protect against a Downgrade Attack, insecure protocols must be disabled on at least one side; just supporting and using secure protocols by default is not enough!
SSH V1 instead of SSH V2
An attacker may try to change the connection parameters between the server and the client when a connection is established between them. According to a presentation at the Blackhat Conference Europe 2003, a cryptanalyst can "force" a client to start an SSH1 session by changing the version number "1.99" of the SSH session to "1.51" instead of SSH2, which means using SSH V1. The SSH-1 protocol has vulnerabilities that a cryptanalyst can exploit.
IPsec
In this attack scenario, the cryptanalyst misleads his victim into thinking that an IPsec session cannot start at the other end (server). This causes messages to be forwarded explicitly if the host machine is in rollback mode.
PPTP
At the stage of negotiating PPTP session parameters, an attacker can force the victim to use a less secure PAP authentication, MSCHAP V1 (that is, "roll back" from MSCHAP V2 to version 1), or not use encryption at all.
An attacker can force his victim to repeat the stage of negotiating the parameters of the PPTP session (send a Terminate-Ack packet), steal the password from the existing tunnel and repeat the attack.
Public means of communication without protection of the authenticity, confidentiality, availability and integrity of information
The most common means of communication for this group is a social network, a public e-mail service, and an instant messaging system. The owner of the resource that provides the communication service has full control over the information exchanged by the correspondents and, at his own discretion, can easily carry out an attack at any time.
Unlike previous scenarios based on the technical and technological aspects of communications, in this case the attack is based on mental aspects, namely, on the rooting in the minds of users of the concept of ignoring information security requirements.
Will encryption save?
Consider the case of a standard HTTP transaction. In this case, the attacker can quite easily break the original TCP connection into two new ones: one between himself and the client, the other between himself and the server. This is fairly easy to do, since very rarely the connection between the client and the server is direct, and in most cases they are connected through a number of intermediate servers. A MITM attack can be carried out on any of these servers.
However, if the client and server communicate over HTTPS - a protocol that supports encryption - a man-in-the-middle attack can also be carried out. With this type of connection, TLS or SSL is used to encrypt requests, which, it would seem, makes the channel secure from sniffing and MITM attacks. An attacker can create two independent SSL sessions for each TCP connection. The client establishes an SSL connection with the attacker, who, in turn, creates a connection with the server. The browser in such cases usually warns that the certificate is not signed by a trusted certificate authority, but ordinary users of older browsers can easily bypass this warning. In addition, an attacker may have a certificate signed by a root CA (for example, such certificates are sometimes used for DLP ) and not generate warnings. In addition, there are a number of attacks on HTTPS. Thus, the HTTPS protocol cannot be considered secure from MITM attacks by ordinary users. [ ] There are a number of measures that prevent some of the MITM attacks on https sites, in particular, HSTS , which prohibits the use of an http connection from sites, Certificate pinning and HTTP Public Key Pinning , which prohibit certificate substitution.
MITM attack detection
To detect a man-in-the-middle attack, network traffic must be analyzed. For example, to detect an SSL attack, you should pay attention to the following parameters:
- Server IP
- DNS server
- X.509 server certificate
- Is the certificate self-signed?
- Is the certificate signed by a certificate authority?
- Has the certificate been revoked?
- Has the certificate changed recently?
- Have other clients on the Internet received the same certificate?
MITM attack implementations
The listed programs can be used to carry out man-in-the-middle attacks, as well as to detect them and test the system for vulnerabilities.
see also
- Aspidistra (English) - British radio transmitter used during the Second World War "invasion", a variant of the MITM attack.
- The Babington Conspiracy (English) - a conspiracy against Elizabeth I, during which Walsingham intercepted correspondence.
Other attacks
- "Man-in-the-browser" (Man in the Browser) is a type of attack in which an attacker gets the opportunity to instantly change transaction parameters, change pages completely transparently to the victim.
- "Meet-in-the-middle" (Meet-in-the-middle attack) is a cryptographic attack that, like the "birthday" attack, uses a compromise between time and memory.
- "Loss in the middle" (Miss in the middle attack) is an effective method of the so-called impossible differential cryptanalysis.
- Relay attack is a variant of a MITM attack based on forwarding an intercepted message to a valid recipient, but not to the intended recipient.
In which an attacker, having connected to a channel between counterparties, intervenes in the transmission protocol, deleting or distorting information.
Principle of attack
The attack usually begins with listening to the communication channel and ends with the cryptanalyst trying to replace the intercepted message, extract useful information from it, and redirect it to some external resource.
Suppose object A plans to send some information to object B. Object C has knowledge about the structure and properties of the data transfer method used, as well as the fact that the planned transfer of the actual information that C plans to intercept. To carry out an attack, C “presents itself” to object A as B, and to object B as A. Object A, mistakenly believing that it is sending information to B, sends it to object C. Object C, having received the information and performing some actions with it (for example, , copying or modifying for their own purposes) sends the data to the recipient itself - B; object B, in turn, believes that the information was received by him directly from A.
Attack example
Injection of malicious code
A man-in-the-middle attack allows a cryptanalyst to inject his code into emails, SQL statements, and web pages (i.e., allows SQL injection, HTML/script injection, or XSS attacks), and even modify user-uploaded binaries in order to to access a user account or change the behavior of a program downloaded by the user from the Internet.
Downgrade attack
The term "Downgrade Attack" refers to such an attack in which the cryptanalyst forces the user to use less secure functions, protocols that are still supported for compatibility reasons. This type of attack can be carried out on the SSH , IPsec and PPTP protocols.
To protect against a Downgrade Attack, insecure protocols must be disabled on at least one side; just supporting and using secure protocols by default is not enough!
SSH V1 instead of SSH V2
An attacker may try to change the connection parameters between the server and the client when a connection is established between them. According to a talk at the Blackhat Conference Europe 2003, a cryptanalyst can "force" a client to start an SSH1 session instead of an SSH2 session by changing the version number "1.99" for the SSH session to "1.51", which means using SSH V1. The SSH-1 protocol has vulnerabilities that a cryptanalyst can exploit.
IPsec
In this attack scenario, the cryptanalyst misleads his victim into thinking that an IPsec session cannot start at the other end (server). This causes messages to be forwarded explicitly if the host machine is in rollback mode.
PPTP
At the stage of negotiating PPTP session parameters, the attacker can force the victim to use a less secure PAP authentication, MSCHAP V1 (that is, "roll back" from MSCHAP V2 to version 1), or not use encryption at all.
An attacker can force his victim to repeat the stage of negotiating the parameters of the PPTP session (send a Terminate-Ack packet), steal the password from the existing tunnel and repeat the attack.
Public means of communication without protection of the authenticity, confidentiality, availability and integrity of information
The most common means of communication for this group is a social network, a public e-mail service, and an instant messaging system. The owner of the resource that provides the communication service has full control over the information exchanged by the correspondents and, at his own discretion, can easily carry out an attack at any time.
Unlike previous scenarios based on the technical and technological aspects of communications, in this case the attack is based on mental aspects, namely, on the rooting in the minds of users of the concept of ignoring information security requirements.
Will encryption save?
Consider the case of a standard HTTP transaction. In this case, the attacker can quite easily break the original TCP connection into two new ones: one between himself and the client, the other between himself and the server. This is fairly easy to do, since very rarely the connection between the client and the server is direct, and in most cases they are connected through a number of intermediate servers. A MITM attack can be carried out on any of these servers.
However, if the client and server communicate over HTTPS - a protocol that supports encryption - a man-in-the-middle attack can also be carried out. With this type of connection, TLS or SSL is used to encrypt requests, which, it would seem, makes the channel secure from sniffing and MITM attacks. An attacker can create two independent SSL sessions for each TCP connection. The client establishes an SSL connection with the attacker, who in turn creates a connection with the server. The browser in such cases usually warns that the certificate is not signed by a trusted certificate authority, but ordinary users of older browsers can easily bypass this warning. In addition, an attacker may have a certificate signed by a root CA (for example, such certificates are sometimes used for DLP) and not generate warnings. In addition, there are a number of attacks on HTTPS. Thus, the HTTPS protocol cannot be considered secure from MITM attacks by ordinary users. [ ] There are a number of measures that prevent some of the MITM attacks on https sites, in particular, HSTS , which prohibits the use of http connections from sites, Certificate pinning and HTTP Public Key Pinning , which prohibit certificate substitution.
MITM attack detection
To detect a man-in-the-middle attack, network traffic must be analyzed. For example, to detect an SSL attack, you should pay attention to the following parameters:
- Server IP
- DNS server
- X.509 server certificate
- Is the certificate self-signed?
- Is the certificate signed by a certificate authority?
- Has the certificate been revoked?
- Has the certificate changed recently?
- Have other clients on the Internet received the same certificate?
MITM attack implementations
The listed programs can be used to carry out man-in-the-middle attacks, as well as to detect them and test the system for vulnerabilities.
see also
- Aspidistra (English) - British radio transmitter used during World War II "invasions", a variant of the MITM attack.
- The Babington Plot (English) - a conspiracy against Elizabeth I, during which Walsingham intercepted correspondence.
Other attacks
- “Man in the Browser” is a type of attack in which an attacker is able to instantly change transaction parameters, change pages completely transparently to the victim.
- "Meet-in-the-middle attack" - a cryptographic attack that, like the birthday attack, uses a trade-off between time and memory.
- "Loss in the middle" (Miss in the middle attack) is an effective method of the so-called impossible differential cryptanalysis.
- Relay attack - A variant of a MITM attack based on forwarding an intercepted message to a valid recipient, but not to the intended recipient.
- A rootkit is a program designed to hide traces of the presence of an intruder.
Write a review on the article "Attack of the intermediary"
Literature
Links
- www.all.net/CID/Attack/Attack74.html
- www.nag.ru/2003/0405/0405.shtml
- www.schneier.com/blog/archives/2006/04/rfid_cards_and.html
An excerpt characterizing the attack of the middleman
“Quartire, quartire, logement,” said the officer, looking down at the little man with a condescending and good-natured smile. – Les Francais sont de bons enfants. Que diable! Voyons! Ne nous fachons pas, mon vieux, [Apartments, apartments… The French are good guys. Damn it, let's not quarrel, grandfather.] - he added, patting the frightened and silent Gerasim on the shoulder.– A ca! Dites donc, on ne parle donc pas francais dans cette boutique? [Well, doesn't anyone speak French here, too?] he added, looking around and meeting Pierre's eyes. Pierre moved away from the door.
The officer again turned to Gerasim. He demanded that Gerasim show him the rooms in the house.
"No master - don't understand... my yours..." said Gerasim, trying to make his words clearer by speaking them backwards.
The French officer, smiling, spread his hands in front of Gerasim's nose, making it feel that he did not understand him either, and, limping, went to the door where Pierre was standing. Pierre wanted to move away in order to hide from him, but at that very moment he saw Makar Alekseich leaning out of the kitchen door opening with a pistol in his hands. With the cunning of a madman, Makar Alekseich looked at the Frenchman and, raising his pistol, took aim.
- Aboard!!! - the drunk shouted, pressing the trigger of the pistol. The French officer turned around at the cry, and at the same moment Pierre rushed at the drunk. While Pierre grabbed and raised the pistol, Makar Alekseich finally hit the trigger with his finger, and a shot rang out that deafened and doused everyone with powder smoke. The Frenchman turned pale and rushed back to the door.
Having forgotten his intention not to reveal his knowledge of the French language, Pierre, snatching the pistol and throwing it away, ran up to the officer and spoke to him in French.
- Vous n "etes pas blesse? [Are you injured?] - he said.
“Je crois que non,” the officer answered, feeling himself, “mais je l "ai manque belle cette fois ci,” he added, pointing to the chipped plaster in the wall. “Quel est cet homme? [It seems not ... but this once it was close. Who is this man?] - looking sternly at Pierre, the officer said.
- Ah, je suis vraiment au desespoir de ce qui vient d "arriver, [Ah, I really am in despair over what happened,] - Pierre said quickly, completely forgetting his role. - C" est un fou, un malheureux qui ne savait pas ce qu "il faisait. [This is an unfortunate madman who did not know what he was doing.]
The officer went up to Makar Alekseevich and seized him by the collar.
Makar Alekseich, parting his lips, as if falling asleep, swayed, leaning against the wall.
“Brigand, tu me la payeras,” said the Frenchman, withdrawing his hand.
– Nous autres nous sommes clements apres la victoire: mais nous ne pardonnons pas aux traitres, [Robber, you will pay me for this. Our brother is merciful after the victory, but we do not forgive the traitors,] he added with gloomy solemnity in his face and with a beautiful energetic gesture.
Pierre continued to persuade the officer in French not to exact from this drunken, insane man. The Frenchman listened in silence, without changing his gloomy look, and suddenly turned to Pierre with a smile. He looked at him silently for a few seconds. His handsome face took on a tragically tender expression, and he held out his hand.
- Vous m "avez sauve la vie! Vous etes Francais, [You saved my life. You are a Frenchman,]" he said. For a Frenchman, this conclusion was undeniable. Only a Frenchman could do a great deed, and saving his life, m r Ramball "I capitaine du 13 me leger [Monsieur Rambal, captain of the 13th light regiment] was, without a doubt, the greatest deed.
But no matter how undoubted this conclusion and the officer’s conviction based on it, Pierre considered it necessary to disappoint him.
“Je suis Russe, [I am Russian],” Pierre said quickly.
- Ti ti ti, a d "autres, [tell it to others] - said the Frenchman, waving his finger in front of his nose and smiling. - Tout a l "heure vous allez me conter tout ca," he said. – Charme de rencontrer un compatriote. Eh bien! qu "allons nous faire de cet homme? [Now you will tell me all this. It is very nice to meet a compatriot. Well! what should we do with this man?] - he added, addressing Pierre, already as his brother. If only Pierre was not a Frenchman, having once received this highest title in the world, he could not renounce it, said the expression on the face and tone of the French officer. To the last question, Pierre once again explained who Makar Alekseich was, explained that just before their arrival this a drunken, insane man dragged away a loaded pistol, which they did not have time to take away from him, and asked that his deed be left without punishment.
The Frenchman stuck out his chest and made a royal gesture with his hand.
- Vous m "avez sauve la vie. Vous etes Francais. Vous me demandez sa grace? Je vous l" accorde. Qu "on emmene cet homme, [You saved my life. You are a Frenchman. Do you want me to forgive him? I forgive him. Take this man away,] the French officer said quickly and energetically, taking by the arm what he had produced for saving his life into Pierre's French, and went with him to the house.
The soldiers who were in the yard, hearing the shot, went into the passage, asking what had happened, and expressing their readiness to punish the guilty; but the officer severely stopped them.
“On vous demandera quand on aura besoin de vous, [When needed, you will be called,” he said. The soldiers left. The batman, who had meanwhile been in the kitchen, approached the officer.
“Capitaine, ils ont de la soupe et du gigot de mouton dans la cuisine,” he said. - Faut il vous l "apporter? [The captain has soup and roast lamb in the kitchen. Would you like to bring it?]
- Oui, et le vin, [Yes, and wine,] - said the captain.
The French officer, together with Pierre, entered the house. Pierre considered it his duty to assure the captain again that he was not a Frenchman, and wanted to leave, but the French officer did not want to hear about it. He was so courteous, amiable, good-natured and truly grateful for saving his life that Pierre did not have the courage to refuse him and sat down with him in the hall, in the first room into which they entered. To Pierre's assertion that he was not a Frenchman, the captain, obviously not understanding how it was possible to refuse such a flattering title, shrugged his shoulders and said that if he certainly wants to be known as a Russian, then so be it, but that he, despite then, all the same forever connected with him by a feeling of gratitude for saving a life.
If this person had been gifted with at least some ability to understand the feelings of others and had guessed about Pierre's feelings, Pierre would probably have left him; but the lively impenetrability of this man to everything that was not himself defeated Pierre.
- Francais ou prince russe incognito, [Frenchman or Russian prince incognito,] - said the Frenchman, looking at Pierre's dirty, but thin underwear and the ring on his hand. - Je vous dois la vie je vous offre mon amitie. Un Francais n "oublie jamais ni une insulte ni un service. Je vous offre mon amitie. Je ne vous dis que ca. [I owe you my life, and I offer you friendship. A Frenchman never forgets insults or services. I offer my friendship to you, I say no more.]
In the sounds of his voice, in the expression of his face, in the gestures of this officer, there was so much good nature and nobility (in the French sense) that Pierre, responding with an unconscious smile to the smile of the Frenchman, shook the outstretched hand.
- Capitaine Ramball du treizieme leger, decore pour l "affaire du Sept, [Captain Ramball, thirteenth light regiment, cavalier of the Legion of Honor for the cause of the seventh of September,] - he introduced himself with a smug, uncontrollable smile that wrinkled his lips under his mustache. - Voudrez vous bien me dire a present, a qui "j" ai l "honneur de parler aussi agreablement au lieu de rester a l" ambulance avec la balle de ce fou dans le corps. [Will you be so kind as to tell me now who I am with I have the honor of talking so pleasantly, instead of being at the dressing station with this madman's bullet in his body?]
Pierre answered that he could not say his name, and, blushing, began, trying to invent a name, to talk about the reasons why he could not say this, but the Frenchman hastily interrupted him.
“De grace,” he said. - Je comprends vos raisons, vous etes officier ... officier superieur, peut etre. Vous avez porte les armes contre nous. Ce n "est pas mon affaire. Je vous dois la vie. Cela me suffit. Je suis tout a vous. Vous etes gentilhomme? [Complete, please. I understand you, you are an officer ... a staff officer, maybe. You served against us It's none of my business. I owe you my life. That's enough for me, and I'm all yours. Are you a nobleman?] - he added with a hint of a question. Pierre tilted his head. - Votre nom de bapteme, s "il vous plait? Je ne demande pas davantage. Monsieur Pierre, dites vous… Parfait. C "est tout ce que je desire savoir. [Your name? I don't ask anything else. Mr. Pierre, did you say? Fine. That's all I need.]
When roast lamb, scrambled eggs, a samovar, vodka and wine from a Russian cellar, which the French had brought with them, were brought, Ramball asked Pierre to take part in this dinner and immediately, eagerly and quickly, like a healthy and hungry man, began to eat, chewing quickly with his strong teeth, constantly smacking his lips and saying excellent, exquis! [wonderful, excellent!] His face was flushed and covered with sweat. Pierre was hungry and gladly took part in the dinner. Morel, the orderly, brought a pot of warm water and put a bottle of red wine in it. In addition, he brought a bottle of kvass, which he took from the kitchen for testing. This drink was already known to the French and got the name. They called the kvass limonade de cochon (pork lemonade), and Morel praised this limonade de cochon he found in the kitchen. But since the captain had wine obtained during the passage through Moscow, he provided kvass to Morel and took up a bottle of Bordeaux. He wrapped the bottle up to the neck in a napkin and poured himself and Pierre wine. The satisfaction of hunger and wine enlivened the captain still more, and he did not stop talking during dinner.
- Oui, mon cher monsieur Pierre, je vous dois une fiere chandelle de m "avoir sauve ... de cet enrage ... J" en ai assez, voyez vous, de balles dans le corps. En voila une (on pointed to his side) a Wagram et de deux a Smolensk, - he showed the scar that was on his cheek. - Et cette jambe, comme vous voyez, qui ne veut pas marcher. C "est a la grande bataille du 7 a la Moskowa que j" ai recu ca. Sacre dieu, c "etait beau. Il fallait voir ca, c" etait un deluge de feu. Vous nous avez taille une rude besogne; vous pouvez vous en vanter, nom d "un petit bonhomme. Et, ma parole, malgre l" atoux que j "y ai gagne, je serais pret a recommencer. Je plains ceux qui n" ont pas vu ca. [Yes, my dear Mr. Pierre, I am obliged to light a good candle for you for saving me from this madman. You see, I've had enough of the bullets that I have in my body. Here is one near Wagram, the other near Smolensk. And this leg, you see, that doesn't want to move. This is during the big battle of the 7th near Moscow. ABOUT! it was wonderful! You should have seen it, it was a deluge of fire. You have given us a hard job, you can boast. And by God, despite this trump card (he pointed to the cross), I would be ready to start all over again. I pity those who did not see it.]
- J "y ai ete, [I was there] - said Pierre.
- Bah, vraiment! Eh bien, tant mieux, said the Frenchman. - Vous etes de fiers ennemis, tout de meme. La grande redoute a ete tenace, nom d "une pipe. Et vous nous l" avez fait cranement payer. J "y suis alle trois fois, tel que vous me voyez. Trois fois nous etions sur les canons et trois fois on nous a culbute et comme des capucins de cartes. Oh !! c" etait beau, monsieur Pierre. Vos grenadiers ont ete superbes, tonnerre de Dieu. Je les ai vu six fois de suite serrer les rangs, et marcher comme a une revue. Les beaux hommes! Notre roi de Naples, qui s "y connait a crie: bravo! Ah, ah! soldat comme nous autres! - he said, smiling, ate a moment of silence. - Tant mieux, tant mieux, monsieur Pierre. Terribles en bataille ... galants ... - he winked with a smile, - avec les belles, voila les Francais, monsieur Pierre, n "est ce pas? [Ba, really? All the better. You are dashing enemies, I must admit. The big redoubt held up well, dammit. And you made us pay dearly. I've been there three times, as you can see. Three times we were on the cannons, three times we were knocked over like card soldiers. Your grenadiers were great, by God. I saw how their ranks closed six times and how they marched exactly to the parade. Wonderful people! Our Neapolitan king, who ate the dog in these cases, shouted to them: bravo! - Ha, ha, so you are our brother soldier! “So much the better, so much the better, Monsieur Pierre. Terrible in battle, kind to beauties, here are the French, Monsieur Pierre. Is not it?]
To such an extent, the captain was naively and good-naturedly cheerful, and wholehearted, and pleased with himself, that Pierre almost winked himself, looking cheerfully at him. Probably, the word "galant" made the captain think about the position of Moscow.
You can almost always achieve the desired result in several ways. This also applies to the field of information security. Sometimes, to achieve the goal, you can brute, independently look for holes and develop sploits, or listen to what is transmitted over the network. The latter option is often the best one. That is why today we will talk about tools that will help to catch valuable information for us from network traffic, using MITM attacks for this.
MITMf
Let's start with one of the more interesting candidates. This is a whole framework for man-in-the-middle attacks, built on top of sergio-proxy. Recently included in Kali Linux. To install it yourself, just clone the repository and run a couple of commands:
# setup.sh # pip install -r requirements.txt
# pip install -r requirements.txt |
It has an architecture that can be extended by plug-ins. Among the main ones are the following:
- Spoof - allows you to redirect traffic using ARP / DHCP spoofing, ICMP redirects and modify DNS queries;
- Sniffer - this plugin monitors login attempts for various protocols;
- BeEFAutorun - allows you to automatically run BeEF modules based on the type of OS and client browser;
- AppCachePoison - performs a cache poisoning attack;
- SessionHijacking - hijacks sessions and saves received cookies in the firelis profile;
- BrowserProfiler - tries to get a list of plugins used by the browser;
- FilePwn - allows you to replace files sent over HTTP using Backdoor Factory and BDFProxy;
- Inject - injects arbitrary content into an HTML page;
- jskeylogger - Injects a JavaScript keylogger into client pages.
If this functionality is not enough for you, then you can always add your own by implementing the appropriate extension.

putty rider
Another noteworthy utility. True, unlike all the other tools considered today, it is very narrowly specialized. As the author of the project himself says, he was inspired to create such a utility by the fact that during penetration tests the most important data was located on Linux / UNIX servers, to which admins connected via SSH / Telnet / rlogin. And in most cases, accessing the administrators' machine was much easier than accessing the target server. Having penetrated the system administrator's machine, all that remains is to make sure that PuTTY is running and use this tool to build a reverse bridge to the attacker.

The utility allows not only sniffing "communication" between the admin and a remote server (including passwords), but also executing arbitrary shell commands within a given session. And all this will happen absolutely transparently for the user (administrator). If you are interested in technical details, for example, how the implementation of the PuTTY process is implemented, I recommend that you read the author's presentation.

A rather old utility that was born more than eight years ago. Designed to clone sessions by stealing cookies. For session hijacking, he has basic skills in detecting hosts (in case of connecting to an open wireless network or hub) and performing ARP poisoning. The only problem is that today, unlike eight years ago, almost all large companies like Yahoo or Facebook use SSL encryption, which makes this tool completely useless. Despite this, there are still enough resources on the Web that do not use SSL, so it's too early to write off the utility. Its advantages include the fact that it automatically integrates into Firefox and creates a separate profile for each intercepted session. The source code is available in the repository, and you can build it yourself using the following sequence of commands:
# apt-get install build-essential libwxgtk2.8-dev libgtk2.0-dev libpcap-dev # g++ $(wx-config --cppflags --libs) -lpcap -o sessionthief *.cpp # setcap cap_net_raw,cap_net_admin=eip sessionthief
# apt-get install build-essential libwxgtk2.8-dev libgtk2.0-dev libpcap-dev # g++ $(wx-config --cppflags --libs) -lpcap -o sessionthief *.cpp # setcap cap_net_raw,cap_net_admin=eip sessionthief |

Proxy Fuzz
ProzyFuzz has nothing to do directly with MITM attacks. As you can guess from the name, the tool is designed for fuzzing. This is a small non-deterministic network fuzzer implemented in python that randomly changes the contents of network traffic packets. Supports TCP and UDP protocols. Can be configured to fuzz only one side. Useful when you need to quickly test some network application (or protocol) and develop a PoC. Usage example:
Python proxyfuzz -l
python proxyfuzz -l |
The list of options includes:
- w - sets the number of requests sent before fuzzing starts;
- c - fuzz only the client (otherwise both sides);
- s - fuzz only the server (otherwise both sides);
- u - UDP protocol (otherwise TCP is used).
The Middler
Presented at the DEF CON conference, a utility for carrying out MITM attacks on various protocols. The alpha version supported the HTTP protocol and had three cool plugins in its arsenal:
- plugin-beef.py - injects the Browser Exploitation Framework (BeEF) into any HTTP request coming from the local network;
- plugin-metasploit.py - injects into unencrypted (HTTP) requests an IFRAME that loads browser exploits from Metasploit;
- plugin-keylogger.py - Injects a JavaScript onKeyPress event handler for all text fields that will be sent over HTTPS, causing the browser to send the user's password character-by-character to the attacker's server before the entire form is submitted.
The Middler not only automatically analyzes network traffic and finds cookies in it, but also independently requests them from the client, that is, the process is automated to the maximum. The program guarantees the collection of all unprotected accounts in the computer network (or public hotspot), to the traffic of which it has access. For the program to work correctly, the following packages must be installed on the system: Scapy, libpcap, readline, libdnet, python-netfilter. Unfortunately, the repository has not been updated for a long time, so you will have to add new functionality yourself.
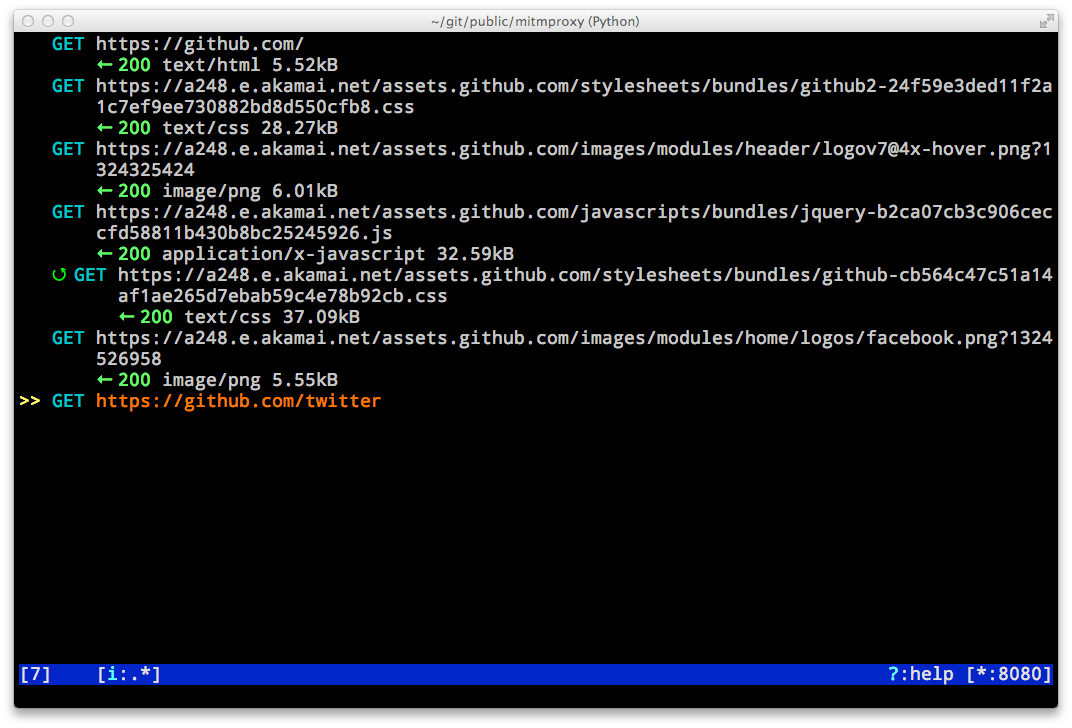
A console utility that allows you to interactively examine and modify HTTP traffic. Thanks to such skills, the utility is used not only by penetration testers / hackers, but also by ordinary developers who use it, for example, to debug web applications. It can be used to get detailed information about what requests the application makes and what responses it receives. Also, mitmproxy can help you learn how some REST APIs work, especially poorly documented ones.
Installation is extremely simple:
$ sudo aptitude install mitmproxy
It is worth noting that mitmproxy also allows you to intercept HTTPS traffic by issuing a self-signed certificate to the client. A good example of how to configure traffic interception and modification can be found.
Dsniff
Well, this utility is generally one of the first things that should come to mind as soon as you hear
"MITM attack". The tool is quite old, but continues to be actively updated, which is good news. It makes no sense to talk in detail about its capabilities; over the fourteen years of its existence, it has been covered on the network more than once. For example, in a guide like this:
or instructions from our website:
Lastly..
As usual, we have not considered all the utilities, but only the most popular ones, there are still many little-known projects that we might talk about someday. As you can see, there is no shortage of tools for carrying out MITM attacks, and, which happens not so often, one of the cool tools is implemented under Windows. There is nothing to say about nix systems - a whole variety. So I guess you can always find the right hijacking tool.
someone else's credentials. Oops, that is, for testing purposes.
 RTSP video surveillance
RTSP video surveillance Broadcasting a video stream from an IP camera using WebRTC
Broadcasting a video stream from an IP camera using WebRTC Why doesn't more always mean better?
Why doesn't more always mean better?