6 ways, how to connect to a WiFi neighbor and protection methods
Unlike corporate access points, neighboring routers are vulnerable much more. With the help of special programs (Wifite, etc.), Wi-Fi is wagoning even without hacker skills. Surely even your neighbors have problems in the router configuration, or do not cost passwords. This article will be useful for those who want to know how to connect to the WiFi neighbor, and those who want to protect themselves from the lovers of freebies.
The hacking method depends on the configuration of the WiFi network of the neighbor. In any safety standard, there are vulnerabilities that can use an attacker for its own purposes.
Open access
Outdoor hotspot is a rare phenomenon, but it exists. Packages are not subjected to encrypts, any user can intercept traffic by applying the AirODUMP-NG utility. The intercepted data is analyzed in Wireshark.
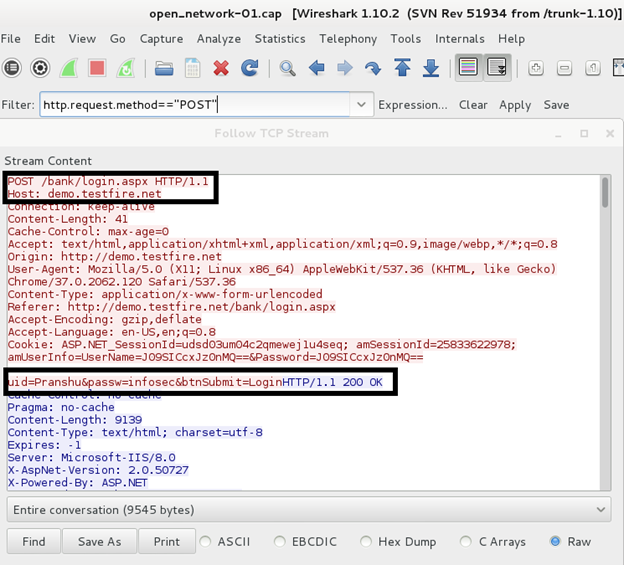
Now it is unlikely, because sites that work with personal data use a secure connection (HTTPS).
Protection method: Put a complex WPA-2 key on the router. If you work through Open Wi-Fi, use the HTTPS EVERYWHERE browser extension, which encrypts traffic.
To search for the nearest open Wi-Fi, you can use the FREE Zone program on Android. In addition, there are some passwords to closed access points (to which users of the program gave access).
IV Collisses in WEP
WEP - an outdated security standard, which is vulnerable to static attacks because of IV-collisions. After the WPA2 network authentication appears, few people use WEP, in the new versions of the firmware it is not even in the settings.
The most effective attack of Tessa-Weinman Pyshkin, proposed in 2007. For hacking, you need to intercept several tens of thousands of packages.
How to protect yourself: change the network authentication method on AES or WPA2 in the router settings.
Selection WPS PIN.
WPS PIN is an 8-digit number, individual for each router. It is wedged by bust through the dictionary. The user installs a complex combination of a WPA password, and not to memorize it, activates WPS-PIN. The transfer of the correct PIN code to the router means the subsequent transmission to the client of the settings, including the WPA password of any complexity.
The main WPS problem is the last digit of the PIN code is the checksum. This reduces the effective length of the PIN code from 8 to 7 characters. In addition, the router checks the code, breaking it in half, that is, it will take about 11,000 combinations to seize the password.
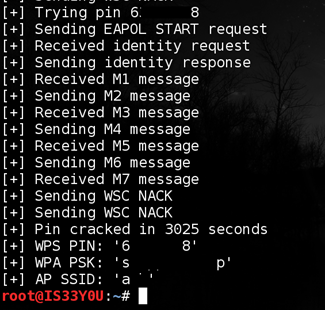
Protection: Update the router firmware. The updated version must have a blocking function activated after several unsuccessful code inputs. If the function is not provided - turn off the WPS.
Other ways to get WPS PIN
Connecting to Wi-Fi by means of a PIN code is possible through direct access to equipment. PIN can be obtained from a router substrate during a "friendly visit".
In addition, the router can remain open, during the firmware update or reset. In this case, the neighbor can enter the router interface using standard login and password, and learn PIN. After that, the WPA password turns out in a couple of seconds.
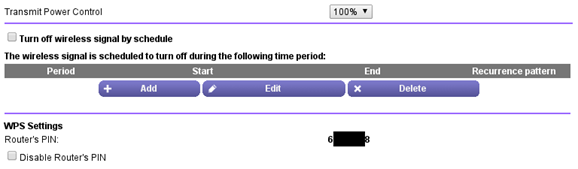
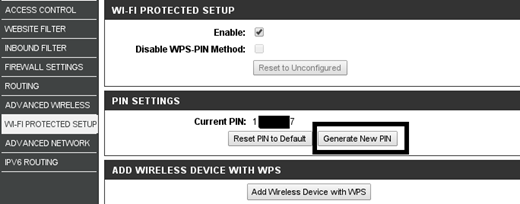
Protection Method: Remove the sticker with a password and do not leave the access point open for a second. Periodically change the WPS PIN through the router interface.
Password Password
Intercepting WPA 4-Way Handshake between the victim and access point, you can extract the dictionary from WPA Handshake.
Protection: Use complex WPA passwords from numbers, characters and letters in different register.
Phishing via wi-fi
If you do not succeed in hacking WiFi programs, use the human factor, to be deceived forcing the user to give the password to the access point.
Phishing attacks are more often conducted via email, but few will write their password for Waifai in the letter. To confuse a neighbor, it's easier to make it connect to another access point. This is done using the WiFiphisher utility written in Python.
The cracking process occurs according to the following algorithm:
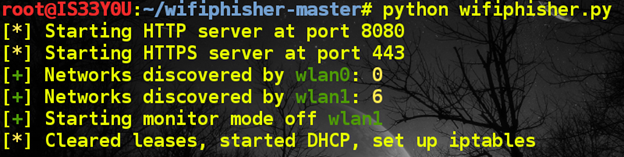
- The utility prepares the attacker's computer: configures HTTP and HTTPS servers, performs WLAN0 and WLAN1 wireless interfaces. Begins to track one of the interfaces found and receives additional IP via DHCP services.
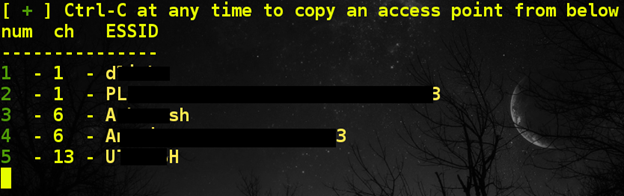
- The console displays a list of access points available for attack.
- The utility clones the name of the selected point and trying to output the current original network.
- The victim falls the Internet and it connects to a cloned access point.
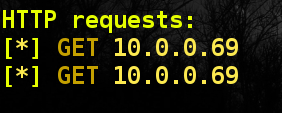
- During connection, an attacker in the console comes information about a new connection.
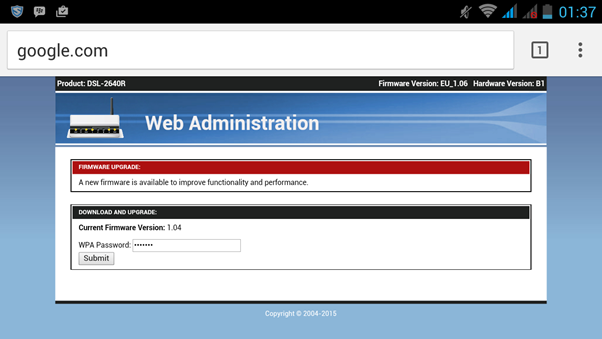
- The victim is trying to open any site, but instead shows a phishing page. For example, instead of Google.ru a connection error will be displayed asking us to re-enter the password. The page can be very similar to the standard page of the provider or the router interface.
- If the victim does not suspect anything and introduces the password, the Internet will work, and the attacker will receive a password in his console.
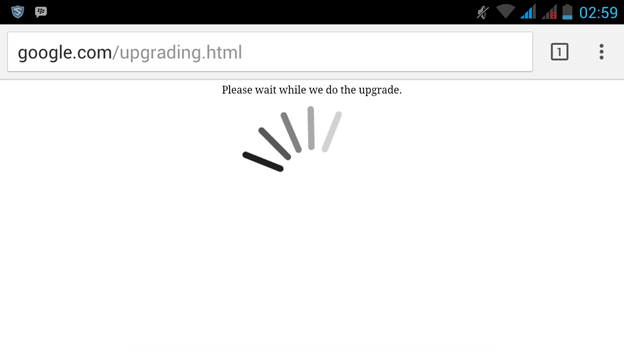
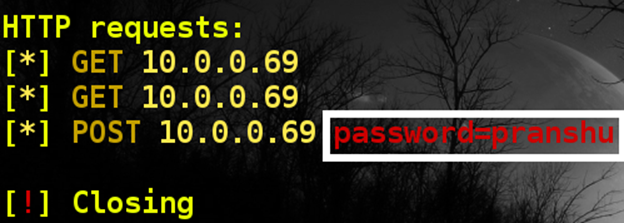
Protection method: Carefully check the pages before entering the password, even if you visit the authoritative site.
Consequences hacking
Access to Wi-Fi opens access to the router settings. And considering that rarely someone changes the standard password to the router interface, information about which is posted on the Internet, the task is greatly simplified. Setup management is the network management.
Getting access to WiFi through hacking will first change the WPS PIN, and after accessing other information for authorization on sites.
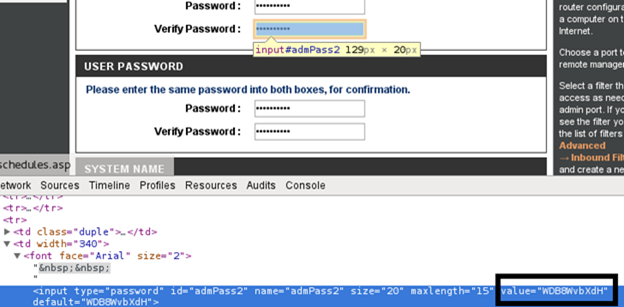
Getting access to Wi-Fi will allow the appropriate utilities to reconfigure the DNS, which will redirect users of banking services to fictitious pages.
If the network is hacked, then even the password change will not help: the attacker will save the WPS PIN or set the Trojan program in the firmware.
Summary
This article is not intended to combine you to hacking the neighbor Vaifa, but to tell about popular vulnerabilities, with the help of which they can cause losses, including material.
Some kindness is not a pity to distribute unlimited Internet, or they do not know how to put a password to access point. Of course, if the neighbors will simply use your unlimited Internet on free, nothing bad for you will not. But so you open access to your passwords. There were cases when people tried to substitute, looking through illegal sites from someone else's IP.
Modern firmware to routers are made as simple as possible and convenient, so even people without experience can configure the security of their Internet through the interface. Use the protection methods described in this article to the maximum, put complex and unique passwords for each resource.
 Service "Prohibition of Calls" from MegaFon
Service "Prohibition of Calls" from MegaFon Tele Support Service2: Free Phone
Tele Support Service2: Free Phone How to connect bluetooth headphones to a computer?
How to connect bluetooth headphones to a computer?